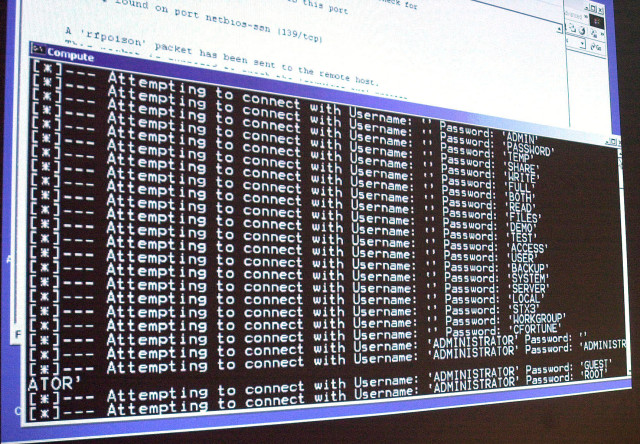
FILE – A computer screen shows a password attack in progress at the Norwich University computer security training program in Northfield, Vermont. (AP)
Whether you go online to check your email, use social media, shop or play games, the odds are you have more passwords than you can keep straight in your head and even more scribbled on enough sticky notes to decorate an entire room. And they just keep getting longer and trickier as cyber attacks become smarter and nastier. It is a cyclical race to find shelter in a password system that is creaking under the pressure.
Enter “Heartbleed” – a vulnerability in the widely-used security software OpenSSL that allows hackers to “bleed” or steal passwords, credentials, and other sensitive information from server memory.
As Kaspersky Lab‘s principal security researcher Kurt Baumgartner explains, the tricky part about this flaw is that “Heartbleed exploits hitting web servers are not necessarily logged as requests because the sensitive server content can be retrieved prior to requesting a resource from the server.”
He says it is “unique and extraordinary” for data bleeding or theft to occur very early in network communications. “On most web servers, all that may be logged is that a connection was set up, which doesn’t give a defender much to work with,” he said in an email interview.
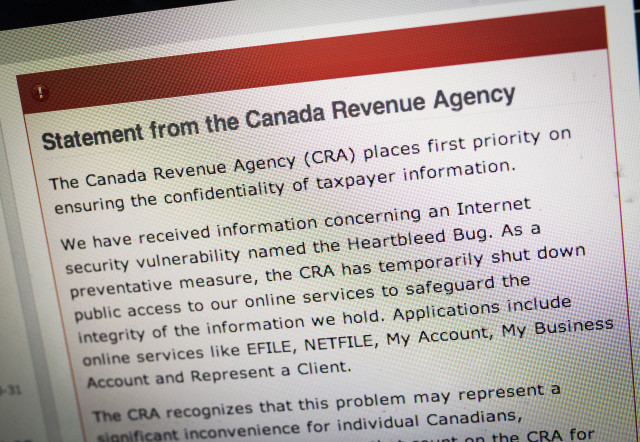
The Canada Revenue Agency website is seen on a computer screen displaying information about an internet security vulnerability called “Heartbleed” in Toronto. (Reuters)
The race is underway to patch the flaw for thousands of websites whose customers’ credentials continue to be at risk.
One of the early casualties was Canada’s tax system. The Canadian Revenue Agency reports that private information of about 900 people was siphoned through the Heartbleed security hole.
Normally, users might buy some time ahead of the next heist by changing their password. With Heartbleed, experts advise consumers to make sure the company has eliminated the vulnerability before they change their password, lest they make the new password available to hackers.
Does Heartbleed spell the end for passwords?
Heartbleed “is simply the most recent example of the fact that we cannot trust our online activities to be secure,” said Jeffrey Carr, Founder and CEO of Taia Global, a cybersecurity firm.
No matter the safeguards, Carr says “the myth of some future secure network as well as the myth that the government somehow has the power to secure our networks remains popular even though there isn’t any proof to support it,” he said in an email interview.
No matter how eager we might be to ditch passwords, they are likely to be around for some time to come. “It really doesn’t matter whether or not passwords, tickets, or keys were used by the authentication process,” said Baumgartner. “The problem is a ‘pre-authentication’ issue, meaning whatever data the server maintains can potentially be grabbed right out of memory.”
That means OpenSSL and similar critical-use software should be “much more thoroughly audited and reviewed,” he said. “I have seen persuasive arguments for formal verification of critical components like these.”
So even if passwords were to be replaced – say with biometrics, “there will always be another way for attackers to compromise valuable data,” said Carr.
Biometrics, by the way, can also be compromised, as demonstrated by a group of German hackers who hacked the fingerprint scanner on Samsung’s Galaxy S5 phone and Apple’s iPhone5S and posted a YouTube video to show how they did it.
Baumgartner is hopeful that passwords will be replaced at some point. But he cautions that they “need to be replaced by an altogether stronger scheme.” He says “threat modeling for authentication schemes seem[s] to have been very narrowly defined by developers.”
While there have been improvements, Baumgartner says “there are so many incredible weaknesses here. Pass the hash and token re-use techniques [i.e., attacks known as authentication token theft and reuse, where stolen data is used to create new authentication sessions] have been extremely problematic for almost a decade now; and the situation is beginning to improve.”
So what’s the answer?
Where businesses are concerned, Carr says firms need to identify and segregate their most valuable data. “Valuable data must be stored on servers that are air-gapped [i.e., insulated from unsecured networks],” he said. “And access to that data must be continuously monitored and controlled in real-time by human beings rather than by automated processes.”
As for individuals, the advice is the same. “The only real protection that the average citizen has is to retreat from Internet usage for any activity which would cause that person harm if compromised,” he said. “That might be sending confidential or potentially harmful information via email, or using online banking if you’re a small business.”
So don’t use those sticky notes for wallpaper just yet. As long as there are software glitches and vulnerabilities, sooner or later, some cyber crook will try to slither through. And until there is a better way to guard private data, vigilance and better passwords will still be needed.
