A woman shows a banking app on her mobile phone in central Bangkok, Thailand, Jan. 5, 2016. Malware targeting banking and payment apps is more prevalent in Asia than in any other region. (Reuters)
Mobile users are more likely to fall victim to cyberattacks in Asia than in any other region, in part because the continent’s Android mobile banking system is riddled with malware, thanks to a lack of awareness and the proliferation of third-party software.
While cybercriminals are likely to attack wherever they can get a foothold, the percentage of attacked users is noticeably higher in China, Vietnam, Malaysia and Indonesia. But South Korea gets the lion’s share of the relatively large number of mobile banking Trojans in the region, according to Kaspersky Lab’s Aleks Gostev, Chief Security Expert for Global research and Analysis.
“This country is number one in the world among the countries most often attacked by banking Trojans,” said Gostev. “A substantial portion of mobile banking attacks in South Korea were caused by representatives of the Trojan-Banker.AndroidOS.Wroba family … designed to steal mobile bank accounts from the largest Korean banks.”
In some countries, the threat is not confined to mobile platforms. Singapore leads the world with the number of users suffering from mobile malware attacks and the number of PCs infected by banking Trojans.
“Among all Kaspersky Lab users attacked by malware in Singapore, 11.6 percent were targeted at least once by banking Trojans throughout the year,” said Gostev. “Austria and Switzerland were next in line at 10.6 percent while Hong Kong, the only other country in the Asia Pacific region, stood in the 8th position at nine percent.”
On the other hand, Western countries like Russia and the United States, for example, either landed toward the bottom of the list of banking malware targets or didn’t make the list at all.
Asia is a particularly attractive target because of its mobile SMS payment modules, popular in China’s highly-competitive gaming market for in-game purchases. The system is besieged by Adware, Trojans and RiskTools applications – legitimate programs with functions that can cause damage if exploited by malicious users.
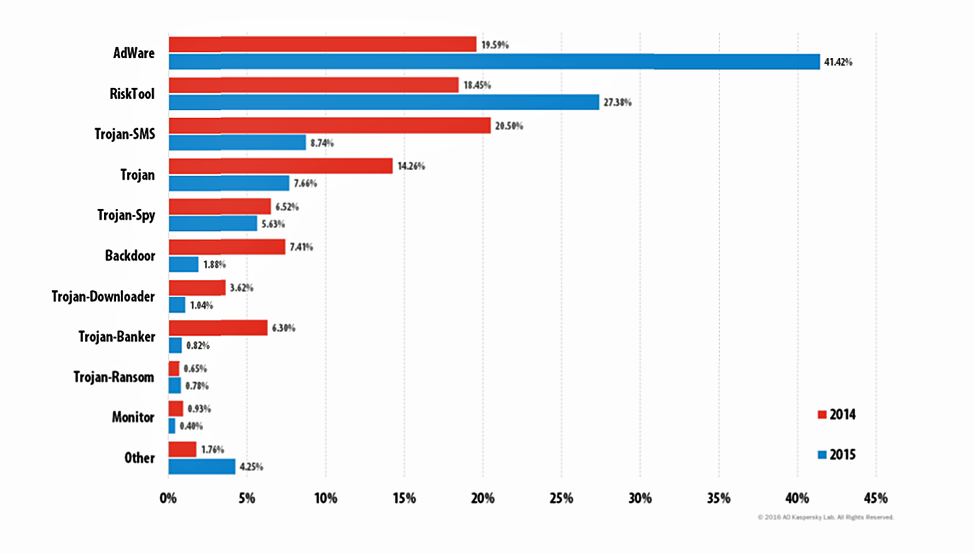
This graph, made available courtesy of Kaspersky Lab, shows the different types of malicious mobile apps attackers use to target their victims.
“Because the games in question are popular, the number of RiskTool applications is constantly increasing,” said Gostev. “… Although AdWare and RiskTool programs do not cause direct harm to users, they can be very irritating, while RiskTool programs installed on mobile devices can lead to financial loss if used carelessly or manipulated by a cybercriminal.”
Through the looking glass
Graphite Software, a company that provides secure banking services, reported similar results. While its researchers found “zero malware” in North American and European banking apps in the Google Play Store, the Asia findings were markedly different, according to Robert Grapes, Vice President of Marketing and Operations.
Working with Coolpad, a Chinese telecommunications equipment company, Graphite created a secure banking space to host a set of curated banking and payment apps. The apps were then processed through a “very stringent process” to ensure that they are free of malware.
“What we found … is a significant issue with malware in apps, but most importantly with financial apps, those being the banking apps, the investment apps, the payment apps,” said Grapes.
A “full 32 percent” of those apps failed the security tests. “So we weren’t able to put them up in the store,” he added. “And these are actually fairly recognizable apps in China – you know, from leading banks.”
The failure constitutes multiple vulnerabilities. Infected apps running on a single Android device can share data and memory processes with whatever else is installed and give hackers access to the entire system.
Graphite is working with the affected parties to raise awareness and help them resolve the issue. But Grapes believes the malware distribution is an inadvertent result of app developers using third-party code libraries – sources of widgets and reusable components that let developers add particular functions to their apps and expedite product packaging and distribution.
Grapes argues that those libraries “are potentially inclusive of malware” and that developers using their resources are “totally unsuspecting, unaware that that even exists.” But he dismissed the notion that banking app developers are “maliciously creating Trojans or backdoors” to compromise their apps.
And since the libraries are not vetted for malware, some of which might not even be created by Asian developers, those who plant the malicious software in the library get access to all sorts of information once their code is executed.
Grapes said vetting the libraries for malware would be a great process to put in place as standard procedure before any app is released into the public domain.
“To me,” he added, “it comes back to a testing exercise, a quality assurance exercise either from the developer of the app itself, or from the store that is posting those apps for public consumption.”
