Posted June 2nd, 2016 at 2:05 pm (UTC-5)

FILE – A teacher helps first grade students during a computer lesson in school in Tallinn, Estonia. (Reuters)
A new app currently in development aims to motivate children to study and excel. But some critics say the controversial cash-for-grades model is ineffective.
Launching first in the U.S. in December, the cash-for-grades e-learning app Incentify is based on the premise that children will be willing to study or do homework chores they don’t want to do in return for cash or other rewards.
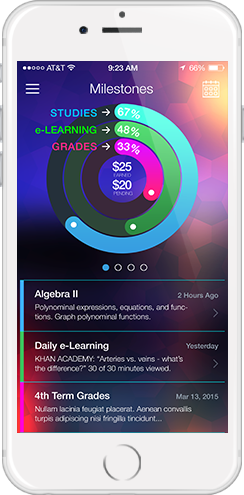
A screenshot from the Incentify cash-for-grades e-learning app, courtesy Incentify’s Patrick Leddy.
“All of our technology is based on Harvard University studies, which have determined … whether kids responded to incentives and did better in school or not,” said Incentify’s CEO and founder Patrick Leddy. “And sure enough, conclusively, they do respond better to incentives.”
Leddy argues that before engaging with teachers and educational content at school, children need to be motivated to study instead of day dreaming or playing games.
“The classrooms are not at the speed of the children,” he told Techtonics. “The children are the Google generation. So how is it that we expect the kids to run at light speed outside of the school, but when they get in the school, they’ve got to slow down to horse and buggy?”
The Google generation – young people with “instant gratification” at their fingertips – can benefit more from e-learning than a traditional classroom, said Leddy. “We know for a fact that e-learning all by itself teaches a kid faster than teacher, pencil, paper and book.”
Dangling “a carrot” in front of kids to entice them to study is a model Leddy intends to take to other parts of the world to empower girls, in particular, who often are married off at an early age.
Whatever the reason for early marriages, Leddy argued children who earn money while learning are unlikely to be sold off for a dowry.
“Once they’re educated, now they could be productive members of society,” he said. “They could be hired or they could start a company … or they could leave because now they have skills to go elsewhere.”
And if the girls get married off anyway, the cash transfers stop.
“We can verify the education,” he said. “That’s the whole key of how our app works. We track all of the kids’ learning performance and metrics. And then we reward them based upon their learning.”
The kids must achieve first. “Nothing transacts until the student has first learned,” he said. “Then the money transacts.”
To do this, Incentify has lined up 72 corporate partners and non-profit groups to reach out to these students and offer them rewards and micro-scholarships through the app.
A screenshot taken with permission from Incentifyed.com website shows progress students have made while using the app to study in return for rewards and incentives.
But Leddy conceded the approach is controversial, with 15-20 percent of people saying kids shouldn’t be paid to perform at school and should do it on their own.
“And you may want to force your child to do that,” he said. “Meanwhile, all of these other kids over here are excelling because they are getting incentivized.”
“This is not the way to solve world poverty,” said Samuel Abrams of Columbia University’s Teachers College, who takes issue with the entire cash-for-grades concept. “You have such huge income disparity in these countries and generations of corruption and abuse. I mean you have a caste system in a lot of these countries.”
Apps can do a lot of things, he said, but he cautioned that there is no “nice, clean silver bullet” to tackle poverty, social justice and the like.
He said the approach is naive and reflects a privileged critique of “poor cultural norms” – bad work habits among low-income communities.
“I don’t buy that at all,” he said in an interview. “I think there are certainly some aspects of underperformance that derive from bad work habits, but that’s probably, most likely the product of horrible discrimination and underprivilege and deprivation.”
Citing the same Harvard study, Abrams said the cash-for-grades model might work in the short-term to get homework done, but in the long-run, passion can only develop through a personal connection between the student, the teacher and the subject matter.
“It comes down to … whether or not it is psychologically good to motivate the kid with cash or gift incentives,” countered Leddy. “Well … they are learning how the world works. They’re performing something for money. …. The bottom line is it works. And it’s proven that it works.”
Leddy hopes Incentify will generate a domino effect on a global scale as children and sponsors who download the app are encouraged to give back a portion of their earnings to help other kids.
“The value of what we’re doing is going to impact generations to come,” he said. “So that’s why we believe it is of the utmost importance getting our technology out there into the world and then letting the kids benefit from it.”













