Software engineer, Philip Jarvis, who has Asperger’s Syndrome, works on Microsoft’s HoloLens mixed-reality device at Redmond, Washington. (Microsoft © Brian Smale)
One percent of the world’s population is on the Autism Spectrum Disorder, a group of complex brain development disabilities. Most are unemployed or under-employed. But several tech companies are now actively courting autistic workers for their unique skills, particularly suited for computing.
Adults on the Autism spectrum excel with analytical skills. They have an eye for detail, exceptional focus, and tolerance for repetition that wears down non-autistic workers. These individuals “tend to thrive in tech-related professions,” said Oliver Thornton, CEO and co-founder of Coding Autism, a for-profit social enterprise that trains adults on the autism spectrum in technology-related skills.
“Someone on the spectrum tends to be more prone to focusing for a longer period of time and not having the mental fatigue to be able to do that task exceptionally,” he said in an interview with Techtonics.
Despite their academic achievement and intelligence, more than 80 percent of autistic adults around the world are either unemployed or underemployed, by U.N. estimates. And the numbers are rising.
“What’s going to happen in 15, 20 years,” asked Thornton, “… when we have a major population on the autism spectrum and they can’t find jobs adequately?”
“There’s a very significant and under-utilized source of talent out there – people that have the right education, the right experience, the right credentials, and that could add value to our companies every day,” said Jose Velasco, head of the Autism at Work program at SAP, a firm that creates software solutions for businesses.
Most of these candidates don’t even make it past the job interview process.
To tackle the problem, several tech companies, including SAP, Microsoft, and Coding Autism, have put in place training and hiring initiatives to attract autistic individuals as part of a much larger effort.
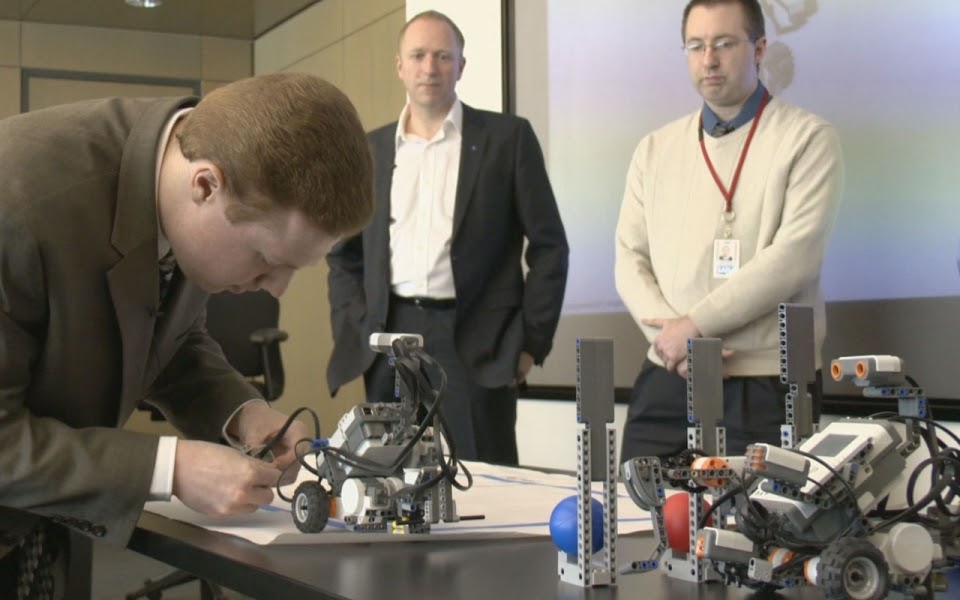
An employee demonstrates a LEGO Mindstorm robot he built as part of the Autism at Work training. The curriculum is designed to see how prospective employees tackle problems. (SAP)
Coding Autism plans to train a maximum of 15 students later this year or early next year. Its specialized curriculum teaches autistic students skills that are in high demand and that “align with their characteristics,” said Thornton, who is also on the autism spectrum. The training helps them find jobs in web development, quality assurance, advanced software skills, and cybersecurity, to name a few.
Students also learn social and job skills, financial management, and career counseling to help them look for work in the technology sector and make it through the job interview process.
Microsoft, SAP, and Hewlett Packard have similar programs with strong support systems. According to Thornton, a lot of the talent these companies look for is in cybersecurity. HP, he added, was so impressed with the outstanding performance of autistic employees that it ramped up recruiting for adults on the spectrum with cybersecurity skills.
Launched in 2013, SAP’s Autism at Work program was driven by a number of factors, including high turnover rates in the tech industry and the significant cost of replacing departing employees – somewhere between “40 to 100 percent of a person that is productive already – yearly salary,” Velasco said in an interview with Techtonics.
Autism at Work trains and hires adults on the autism spectrum in nine countries, including India, Argentina, and Brazil, the U.S., and several European countries. The program prepares candidates for job interviews and provides them with the resources and structure they need to succeed in software testing, graphic design, customer support, software development, cybersecurity, and other areas.

Jeff Wang, a SAP employee participating in the Autism at Work training program, learns how to use presentation tool Prezi and shares an overview of what he learned in training with a room full of managers. (SAP)
It is a surreal feeling of not only making a living, but also feeling valued that I get [to] share my perspectives and learn new skills,” he said in an email. “It also means feeling assured that I have a strong support system and resourceful connections who [are] always willing to help – SAP Employee Jeff Wang
“We are capturing really very smart, very brilliant people,” said Velasco. “… Our colleagues are doing a fantastic job because they have a very strong attention to detail on tasks that require a lot of concentration.”
For a high-tech company like SAP, fresh talent and perspectives are crucial for innovation. “New products are only created when you bring in different perspectives into the creative process,” he added.
“The diversity of our workforce and inclusion of talented people from different backgrounds is the fuel that keeps the engines of innovation and growth running,” said Microsoft’s Director of Inclusive Hiring and Accessibility, Neil Barnett, in an email.
Microsoft, which started an autism hiring program in 2015 to increase workforce diversity and utilize untapped potential, already has 32 autistic candidates on board as software engineers and data scientists, among other roles. They receive the same benefits and compensations as full-time employees.
“People with autism bring strengths that we need at Microsoft, such as pattern recognition, the ability to think at a very high level of detail and depth, and/or excel in math or code,” said Barnett.
The program was created with a focus on adjusting Microsoft’s hiring process “to better suit the needs of people with autism.” It is “a unique way to find qualified candidates who were not making it to Microsoft through a traditional interview process,” he said.
Microsoft’s autism program and those at SAP and Coding Autism are slowly falling under a bigger umbrella – a nascent school of thought that argues that “neurodiversity” is a natural condition of the human genome.
Earlier this year, SAP held its second Autism at Work Summit, with participation from technology and private firms, the public sector, academia, and philanthropy to promote neurodiversity and encourage more companies to consider hiring autism spectrum job seekers.
“It is not only the right thing to do,” said Velasco, “but it’s going to accelerate the implementation of these programs and also the accuracy – the way in which they are implemented.”