2017 is here and this is as good a time as any to find ways to turn those New Year Resolutions into reality. There are a few apps that help with that and more. Some are free, though they will track you and your information. You’ll have to pay for some of the others if you want them. Techtonics sifted through some of the latest and came up with this bundle.
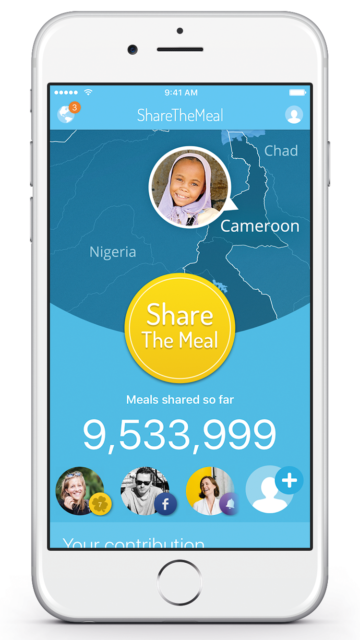
ShareTheMeal
This World Food Program’s nonprofit app lets users feed a hungry child with a single tap on your smartphone. Users can donate US $ 0.50 to feed a child for a day and track the activities of the program with their friends. The app has already shared more than 10 million meals.
There are other apps that offer a different approach to giving, if that was high on your New Year’s resolutions list. Exercise-minded individuals can use Charity Miles Walk&Run Tracker while running, biking and walking to donate to charity. Brand name sponsors will donate to a charity of your choice for every mile you cover or earn you money that can be donated to your charity.
Donate a Photo for Charity is a free donation app from Johnson & Johnson. The company donates $1 to a charity of your choice for every photo that you donate. The picture can be about any subject, but it’s probably best not to donate personal pictures. And be sure to remove the geocoding metadata from the pictures if you prefer not to share your location.
MotherToBaby
The nonprofit Organization of Teratology Information Specialists (OTIS) launched MotherToBaby as it marks Birth Defects Prevention Month this January. The app provides evidence-based information about pregnancy and breastfeeding exposures.
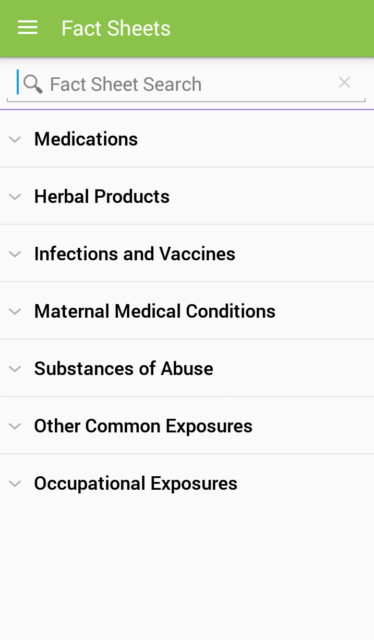
A screenshot from the MotherToBaby app, which provides pregnant women with all sorts of information to keep them informed about potential risks to their babies. (OTIS)
In an emergency, the app can link users to information experts who can offer more customized support in real-time. Users of MotherToBaby also have the option to volunteer their pregnancy information to benefit research.
OTIS said in an email it believes the app will benefit English and Spanish-speaking countries in the developing world. But the group hopes to expand the app’s reach in the future.
Trusted Contacts
Google’s Trusted Contacts is a personal safety app that lets family and friends added as trusted contacts ask for the user’s location. While the request can be denied, the feature is helpful in emergencies or when the user is in an unsafe environment. The app lets trusted contacts check on the users’ phone activity to make sure they are safe.
Decrypto
As ransomware attacks continue to escalate, there are now a few apps that help victims decrypt their files. If you find yourself looking at an encrypted message, Decrypto, the latest in a bunch of encryption and decryption apps that rolled out over the past year, can identify the cipher and decrypt the message. It also lets you encrypt your messages. Other app include Cypher Solver, and Cryptography, which includes in-app purchases.
Forest
Forest offers a unique solution to help people who can’t seem to part with their smartphones, whatever the circumstances.
The app asks users to plant a seed whenever they need to focus on their work . Eventually, the seed will grow into a tree. But it will wither and die if you cannot resist checking Facebook or Pokémon GO every so often. The app is designed to prevent users from using other apps during the planting session.

(Forest)
Forest also partners with Trees for the Future to plant real trees. They have projects in Cameroon, Kenya, Senegal, Uganda and Tanzania.
7 Minute Workout Challenge
If fitness was high on your 2017 to-do list, the 7 Minute Workout Challenge offers 12 exercises that can be done, well, in 7 minutes. The app tracks your progress and encourages you to persist, though it’s always good to check with your doctor first if you are concerned about any of the exercises.
Another option is Full Fitness Exercise Without Trainer, which was just updated. The app offers exercise routines and calorie-counting while helping users resolved to lose weight keep track of their goals. But if exercise isn’t for you, Calorie Counter & Diet Tracker can help you keep those calories in check.
Sidekix
Sidekix is an urban navigator, trip planner and map all in one. The iOS and Apple Watch app uses your smartphone’s location and GPS features for interest-based routing. That means it can find shopping, cultural or dining spots based on your personal interests. It suggests events, best routes, and directions to help you reach your destination. Sidekix is available in about 100 cities in the United States, Europe and Israel, and more will be added.
If you are privacy-oriented, you should read the developers’ policies before downloading any of the tracking apps.